Some of us think of fax machines as a relic, but fields like healthcare and government still rely on faxes every day. Researchers have discovered serious vulnerabilities in fax machines that could let cybercriminals infiltrate any home or corporate network with just a fax number.Known as ‘Faxploit,’ the vulnerability research by Check Point’s Yaniv Balmas and Eyal Itkin illustrates how a hacker could easily exploit fax protocol and infiltrate a network. To begin, corporate fax numbers are typically posted on websites and business cards. Using that number, a hacker could send an infected file to the corporate fax machine as a way to launch a beachhead for a larger attack.
“The attack scenario is actually pretty simple,” Check Point’s Itkin says. “A malicious attacker wants to infiltrate a covert network, let’s say a bank. The fax number for this bank is public, so he can get that number. On the bank side, if the printer that receives the fax is also connected to the internal network, then all the attacker needs to do is send a malicious fax to this phone number and automatically he will be inside the internal network of this bank. It’s crazily dangerous.”
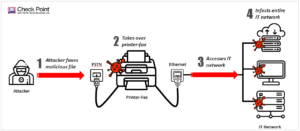
Hackers have targeted fax machines for decades, and the technology is still insecure in basic ways. For example, fax data is sent with no cryptographic protections; anyone who can tap a phone line can instantly intercept all data transmitted across it. “Fax is perceived as a secure method of data transmission,” says Balmas. “That’s a huge misconception—it’s absolutely not secure.”
What can you do to secure your network?
- Best way, move to a service such as eFax where it limits exposure and transmission is secure.
- Most simplistic way is to unplug the network cable from the fax machine.
- Check with the fax machine’s manufacturer for a software patch and update it.
- Segment your network so the attack cannot spread into the rest of the network.
In conclusion, our world becomes more connected through IoT (Internet of Things) devices, which opens doors to allow potential hackers to infiltrate IT networks and provide unauthorized access to sensitive information. It is important to understand what you are plugging into the network and how it will affect the rest of your network security-wise.
Credits
https://blog.checkpoint.com/2018/08/12/faxploit-hp-printer-fax-exploit/









